 Knowing is half the battle. No, it’s not a public safety advice from a Saturday morning cartoon. It’s a very important adage to remember when facing challenges, battles and war. It’s synonymous to ‘know thy enemy’ which is apparently what China is trying to do. It’s what it’s been allegedly doing ever since the country gained prowess in cyberspace, in other words, hacking. And from what recent history tells us, they seem to be getting to know the United States very well. So yes, the recent alleged hacking by China of the United States Office of Personnel Management is nothing new. Will these attacks continue and become the norm? If the United States is so vulnerable, what can any government do to not get hacked?
Knowing is half the battle. No, it’s not a public safety advice from a Saturday morning cartoon. It’s a very important adage to remember when facing challenges, battles and war. It’s synonymous to ‘know thy enemy’ which is apparently what China is trying to do. It’s what it’s been allegedly doing ever since the country gained prowess in cyberspace, in other words, hacking. And from what recent history tells us, they seem to be getting to know the United States very well. So yes, the recent alleged hacking by China of the United States Office of Personnel Management is nothing new. Will these attacks continue and become the norm? If the United States is so vulnerable, what can any government do to not get hacked?
Currently, the two superpowers, China and the United States are currently at odds because of China’s activities in the East and South China Sea. But even before then, China has been accused of hacking and stealing very sensitive private and government information. Information that could jeopardize the stability of the United States right down to its national security. The most recent incident of which is what happened with Office of Personnel Management where the information of 1.9 million federal employees were stolen. Information dating back to 1985. The hack was apparently traced back to China but the Asian state as usual denies any wrongdoing with rhetoric reprisals and is even prepared to counter the accusations.

So what else was the great tiger, dragon or panda up to as far back as 2005? Are they really so talented as to be able to penetrate some of the world’s most secure agencies and corporations? Were these entities that secure in the first place?
- The ability to hack in and steal information from US military contractors like Lockheed Martin is a grave cause of concern. Some governments would have gone to Defcon 3 instead of diplomatically trading accusations of hacking over CNN. But it happened last year when China allegedly hacked into technology companies, US airlines and defense contractors assigned with critical information on troop and equipment logistics as per the Senate Armed Services Committee.
- Another instance was when a Chinese employee named Lizhong Fan took off with a wealth of information stored on several hard drives from the Arizona Counter Terrorism Information Center. Also, according to the Wall Street Journal, Chinese hackers have been milking Nortel for information for almost ten years by using stolen passwords from executives.
- Again in 2014, five Chinese military hackers were indicted by the FBI for trying to obtain information from various US energy and metals companies for use by the Chinese government or competing Chinese companies. Oil and gas companies have also fallen victim as far back as 2009.
- Companies like Google were not immune to such hacks as the company suffered an attack intended to steal intellectual property back in 2010. In 2011, Gmail accounts belonging to senior government officials, journalists and activists have been hacked but whether those accounts belonged to the United States or China or both are unknown.
- And lastly, security firm McAfee uncovered a hacking campaign known as operation Shady RAT which has been going on as early as 2006 targeting not just the US government agencies but the UN, technology companies and defense contractors.
Many of these hacking incidents can be traced back to China but other rogue states such as Iran or North Korea may be just as guilty. Unless the CIA come up with definite proof (if they’re not busy getting hacked), the US government or any other government for that matter should be extra careful and beef up their security measures. Not just technically but procedurally as well. There’s no knowing how advanced China’s, Iran’s and North Korea’s hacker infrastructures are and how they manage to penetrate the perceived most secure networks on the planet. With such very sensitive information, the guilty party now has intimate knowledge of the enemy and has apparently declared war in cyberspace and can use all that info to directly challenge the US in the physical world.
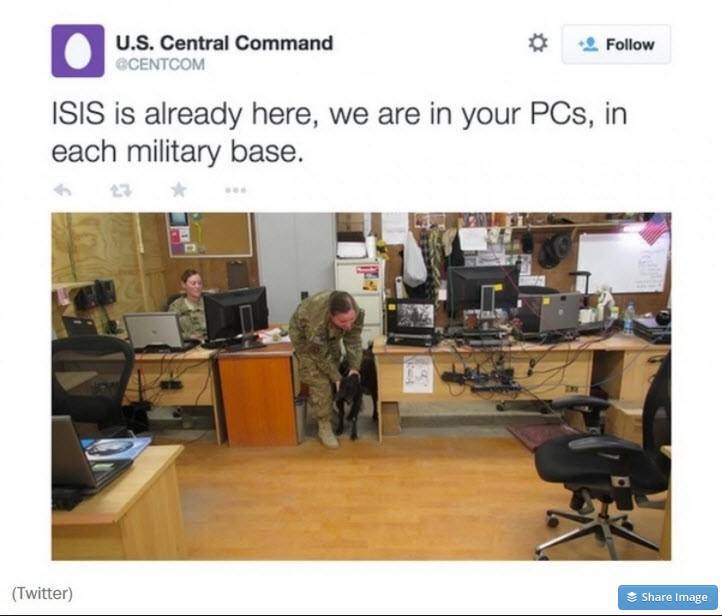
But directly accusing another state of espionage through hacking is not in the best interests of both nations but the espionage itself must be immediately addressed. For all we know, some 15 year old kid in some basement is actually orchestrating conflict all because we’re careless when it comes to security. In almost every movie involving hackers, it takes just a couple of minutes for a hacker to get to the FBI’s password screen and crack it. Is that really the case? If so, the attacks can only continue and get worse. Governments and corporations need to improve their security in order to stave off these attacks. Measures such as keeping very sensitive information out of internet connected computers; wiping or destroying storage media after the transfer of important information; encryption of sensitive data; regular password changes for important personnel or switching to biometrics and regular security briefings and checks of staff. And let’s not forget ISIS who is not laying claim to taking military websites offline.
If we’re not careful, forget the NSA. China might also know where you are and what you’re up to. Oops, forgot to tape my webcam.

