We live in lazy, convenient times where word processors correct our spelling and grammar automatically, where browsers auto-complete or auto-suggest website URLs. We sometimes take these things for granted that they backfire. When they do we disable them or ignore them like those often flawed auto-correct features on our mobile phones. Even the best of us can commit mistakes when we type, believing too much on our touch-typing skills or that auto-complete feature of our brains that a word is correct as long as the first and last letters of a word are in place. But in a world now full of malware, being complacent and leaving out details is something we can no longer afford.
URLs
Make no mistake. Make sure that you spell your top-level domain extensions correctly or you could end up in a very bad place called Malwareville. Typing those .com, .net, .biz extensions incorrectly could accidentally take users to a different website. For example, typing Netflix.om instead of Netflix.com can take you to a site that looks like Netflix but will ask you to install an “updated” plugin for the site to continue loading, which of course unsuspecting users would install in a hurry. That plugin actually installs some form of malware into their computers.
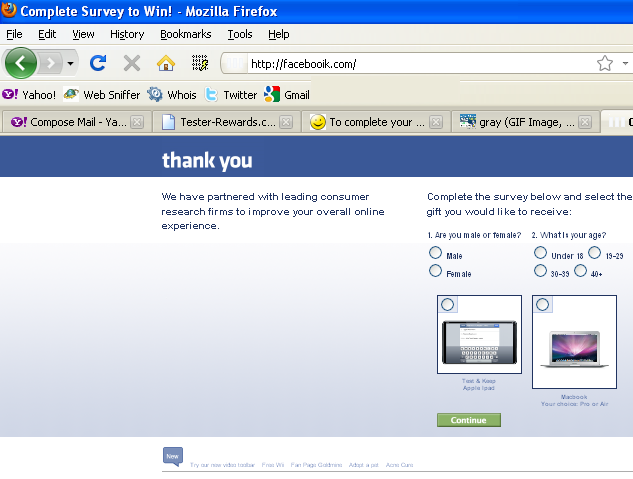 The extension .om is actually a valid one and stands for the country code top-level domain for Oman. It’s, unfortunately, being used by cybercriminals into setting up phony versions of major websites, all hoping that someone might accidentally make a typo and omit the ‘c’ in .com when visiting a website. This technique is called typo-squatting which turns a domain extension typo into a valid destination and posing as the intended website. This technique could apply as well to mistyped URLs such as Netlix.com or Netflx.com. As many as 300 malicious websites exist that take advantage of typo-squatting according to security vendor Endgame. These websites can trick users into installing malware unintentionally or install them by force. These websites can redirect users to ads, phony surveys, and untrustworthy URLs. Valid websites can correct these problems legally should more reports of typo-squatting reach them but in the meantime, make no mistake with your URLs.
The extension .om is actually a valid one and stands for the country code top-level domain for Oman. It’s, unfortunately, being used by cybercriminals into setting up phony versions of major websites, all hoping that someone might accidentally make a typo and omit the ‘c’ in .com when visiting a website. This technique is called typo-squatting which turns a domain extension typo into a valid destination and posing as the intended website. This technique could apply as well to mistyped URLs such as Netlix.com or Netflx.com. As many as 300 malicious websites exist that take advantage of typo-squatting according to security vendor Endgame. These websites can trick users into installing malware unintentionally or install them by force. These websites can redirect users to ads, phony surveys, and untrustworthy URLs. Valid websites can correct these problems legally should more reports of typo-squatting reach them but in the meantime, make no mistake with your URLs.
Attachments
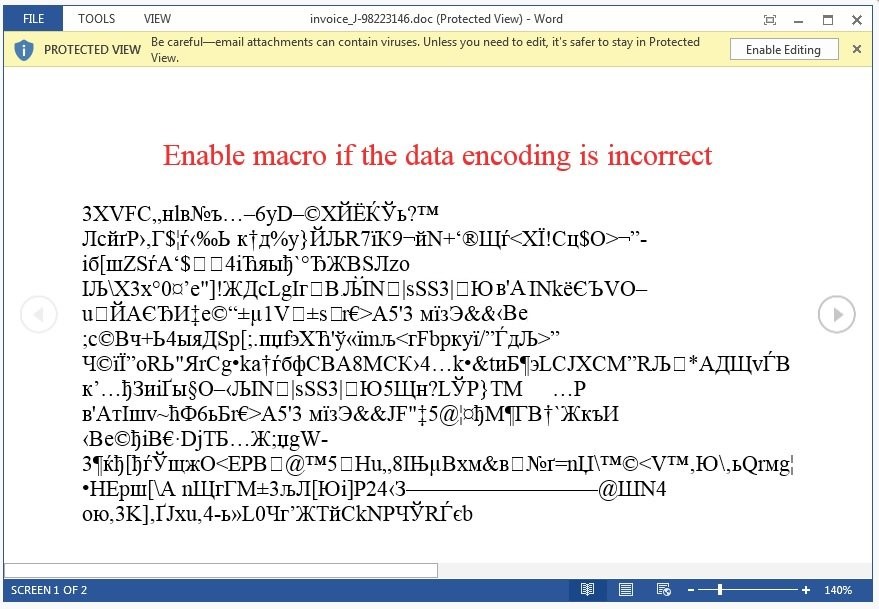
Another thing users should not make any mistakes on—opening email attachments from suspicious sources. Though sometimes, the sources themselves are trustworthy but their attachments aren’t. Malware is often delivered to unsuspecting users in the form of a macro-enabled Word attachment. The latest is the ransomware KeRanger which targets Macs. Due to the rising popularity of Macs as Windows alternatives, hackers and malware authors have started targeting them. Some of the aforementioned typo-squatting websites target Macs exclusively. Another dangerous ransomware delivered via Word document disguised as a scrambled invoice form is Locky. Locky prompts the user to enable macros to ‘unscramble’ the attached invoice. It later downloads parts of itself to the user’s computer and encrypts important files where the only solutions include, restore from backup or pay the heathens and reformat the system. This time, Locky affects Windows users, and they’ll know it when they notice a bunch of scrambled file names in place of their files with a text file notice on how they can be unencrypted. This could make users rue the day they’ve ever heard about encryption.
Palo Alto Networks has also reported another similar malware which does not download files but instead uses Windows PowerShell to do its damage. This yet unnamed malware also targets business email addresses and uses them to propagate. Users tend to open attachments straight from their colleagues before checking. Criminals have now upped their game by going after specific targets and compose their emails so they’d look as legitimate as possible. This time, by using PowerShell itself, this new malware is tough to detect.
 Your Uber Driver
Your Uber Driver
Speaking of malware, is the Uber app itself a form of malware? One that can control the minds of people into doing stuff? Like killing. Not really, but it’s an idea. Don’t be too trusting to an app or its promises. The thing could be just useless or turn out to be a spy like fake battery management apps. As for Uber, it’s them that should make no mistake in accepting drivers. If background checks were possible, incidents of rape, theft and murder would be avoided. Commuters, however, can’t exactly choose their Uber drivers like this gut from Michigan, who killed 6 people and accused Uber that their app controlled his mind. Yes, the Uber app hacked into his mind and encrypted parts of it enabling him to commit murders and come up with such a preposterous notion to get an insanity plea. That or the Kingsman movie might be on to something.
So to avoid any hassles, just protect yourselves. Keep your anti-virus, anti-malware software updated. Type URLs carefully, inspect your attachments, keep your macros disabled as much as possible and don’t forget your taser or pepper spray when you go out.