Built into Windows 10 is the Windows Defender Advanced Threat Protection first announced in March last year. It’s a service designed to help enterprises detect, investigate, and respond to advanced attacks on their networks. It provides a new post-breach layer of protection to help detect threats that have made it past other defenses. Microsoft is urging enterprises to do a Frozen and let go of their Windows 7 or older setups, claiming that Windows 10 can stop ransomware in case it gets past initial defenses.
Microsoft is, of course, spinning that older Windows versions can no longer meet today’s high-security requirements of IT departments. The company is no longer inclined to continue providing support for older Windows versions and will soon cease to support Windows 7, but with Windows 10, the additional security provided by Windows Defender Advanced Threat Protection is conveniently built in since the Anniversary Update. According to the Windows Defender ATP blog, several companies who opted to test initial releases of the package were satisfied with its performance.
The Anniversary Update version of the ATP, through behavioral algorithms, managed to block zero-day exploits such as the activity to download a ransomware payload done through Powershell to connect to a TOR site and displayed an alert. ATP is also able to detect efforts by ransomware to prevent recovery efforts and the actions the malware takes just before it encrypts files.
“Security operations center (SOC) personnel could use such alerts to get the source IP and block this IP address at the firewall, preventing other machines from downloading the executable…”
— Tommy Blizard
With the upcoming Creators Update due to be released in April, more defense features for Windows Defender ATP will be added including sensors to detect in-memory malware and kernel level exploits as well as better tools to conduct forensics and isolate infected machines.
“Our research into prevalent ransomware families reveals that delivery campaigns can typically stretch for days or even weeks, all the while employing similar files and techniques. As long as enterprises can quickly investigate the first cases of infection or ‘patient zero,’ they can often effectively stop ransomware epidemics,”
— Tommy Blizard, Microsoft Windows Defender ATP research team
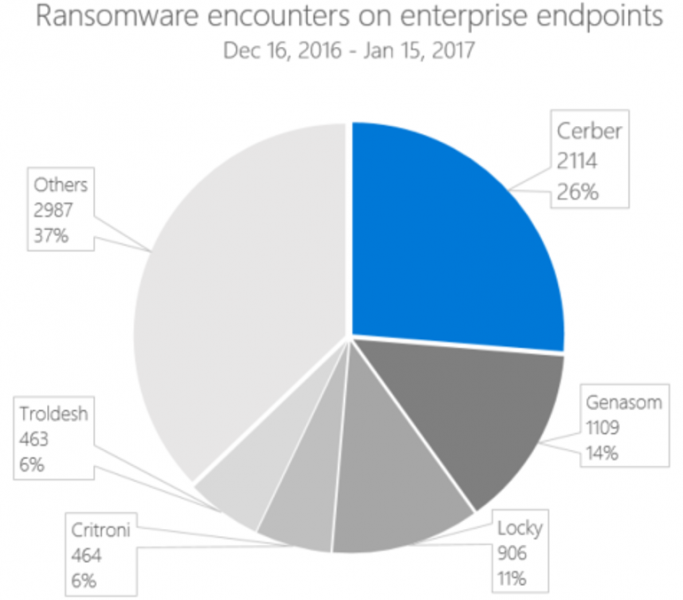
Most ransomware out in the wild are forks of a ransomware called Cerber and the research mentioned above was done based on encounters from enterprise customers between December 16, 2016 and January 15, 2017. Since these ransomware work in similar ways, Windows Defender ATP was able to detect and counter them. Hopefully, Windows Defender ATP also works on non-Cerber-based ransomware.
Through personal experience, ransomware is terribly dangerous, especially without any backup strategy. Heck, any virus or media breakdown is dangerous without a backup strategy, so keep backups handy at all times, unlike other victims who had to pay through the nose and had to familiarize themselves with bitcoin to do so. Microsoft is now actively protecting our network against further incursions of our previous ransomware as well as upgrading newer machines to Windows 10. This is not a shill ad mind you though Microsoft could probably throw a few bucks our way. Another effective free anti-ransomware app you could use is Cybereason’s RansomFree.